IdeaData Review
What is IdeaData?
CySight by IdeaData is an integrated cyber and network intelligence solution that assists organizations in saving time and money in monitoring, maintaining, securing, and managing their network. It lets you obtain analytics and insights about everything passing through your network in a granular manner. Unifying all the tools they need for attaining enhanced network traffic/flow visibility and control, CySight caters to business leaders, network architects and administrators, cyber and security specialists, data center managers, and capacity planners.
Users can detect and analyze network traffic without using invasive techniques like probes. CySight uses different networking technologies and variants, including NetFlow, sFlow, IPFIX, jFlow, VMware, and Netstream. Network flow logs from cloud providers and extended metadata from technology partners are provided as well.
They can also track bandwidth usage across Network-enabled devices and user interfaces based on various parameters. CySight allows them to filter reports using any NetFlow data fields, perform real-time and long-term flow analysis and reporting, and drill down into the root causes of trends from long-term reports.
With its baselining feature, users can compare data about locations, applications, servers, interfaces, IPs, and other elements against specific baselines at any time. Moreover, the cyber and network intelligence tool can gather forensic or traffic data at different levels of granularity, like on a per hour or minute basis. It can also quickly discover, classify, isolate, and mitigate cyber threats, attacks, anomalous events, and malicious traffic.
Show MoreOverview of IdeaData Benefits
Network Performance Visibility
CySight provides users with absolute network visibility to immediately identify and address performance, downtime, and security problems that might pose risks to the continuity of their business operations. Using CySight’s data collection tuning capability, they can capture, retain, and analyze network data at different levels of granularity. For instance, they can gather information about traffic, conversations, and transactions from various parts of the network on a weekly, hourly, or minute basis.
With the baselining feature, they can set baselines that you can use for conducting a comparative analysis of macro and micro-level elements of their network, encompassing locations, applications, servers, interfaces, and IPs. Users can compare actual data about specific or combinations of elements against the baselines for different periods. This feature helps them identify and assess utilization patterns, abnormal events, end-user experiences, and infrastructure-related impacts across network resources.
Security Forensics
The cyber and network intelligence solution enables you to implement granular, flexible, and scalable security forensics. It provides data analysis, auditing, and forensic reporting tools and features that allow you to discover and address network security vulnerabilities, threats, breaches, and attacks. You can build and customize templates and data fields and analyze network data from multiple perspectives.
CySight lets you analyze network traffic based on packet size, standard deviation, and record count. This way, you’ll easily discover anomalous network traffic, spammy network conversations, DDoS or malware attacks, and rogue applications. You can also set up automated alerts to notify you and your teams about analysis results and immediately take appropriate actions to mitigate and fix issues.
Cyber Threat Intelligence
CySight delivers all the essential information you need to protect your network from various forms of cyber threats. Artificial intelligence and machine learning algorithms automatically and intelligently run diagnostics across all your physical networks and cloud services and detect outliers, deviations, anomalies, and vulnerabilities.
You’ll be warned about advanced persistent threats, insider threats, DDoS, worm, and ransomware attacks, and malicious flows ahead of time. Furthermore, CySight enables you to access continuous global streams of data regarding existing and emerging threats.
Show MoreOverview of IdeaData Features
- Network Performance Analytics
- Baselines
- Analysis Tools & Methods
- Granular Data Collection
- Network Usage Monitoring
- Network Bandwidth Monitoring
- Security Forensics
- Threat Intelligence
- Anomaly Detection
- AI Diagnostics
- Real-Time & Long-Term Reports
- Filtering Feature
- Cloud Services Analytics
- Scalable Solution
What Problems Will IdeaData Solve?
1. Providing Flexible Reports with Context: Company “A” wanted to make better use of their data, not just in identifying who the big bandwidth abusers are, but primarily to enhance the ability to find information based on the data collected to find and solve issues, both network and security related. Contextual and flexible reporting provided a complete understanding of the traffic traversing across the whole network and different subsections of the network.
2. Detecting Data Breaches & Leaks in Real-Time: CySight supports network and security forensics analysis and reporting in a granular approach. It lets organizations discover and resolve security breaches happening in real-time or for quite a long time, such as data leaks. They no longer need to rely on the standard security systems and devices that don’t provide them the capability to capture, report, and analyze the granular details of every transaction. CySight uses technologies like P2P tools to capture and report even the tiniest traffic and data often undetected by other networking tools. This way, SOC and NOC teams can efficiently utilize all the information they need for monitoring and securing their networks.
3. Malware & Ransomware Hunting: Pichael is a SOC engineer at a large enterprise that needs to constantly monitor his organization’s network and cloud environments. Once he discovers an anomaly, he reposts so to the incident response team. To now follow the breadcrumbs, the incident response team needs as much contextual information from the data as possible. When investigating an incident, be it a network issue or malware to be dealt with, CySight provides granular and scalable retention that provides teams to understand who is doing what, where, when, with whom, and for how long.
Awards & Quality Certificates


IdeaData Position In Our Categories
Bearing in mind companies have special business-related requirements, it is only logical that they avoid purchasing a one-size-fits-all, ideal solution. Nevertheless, it is nearly futile to chance on such application even among recognizable software products. The logical step to do is to write the varied major functions that necessitate inspection like major features, price plans, skill aptitude of staff, company size, etc. After which, you must double down on your research thoroughly. Browse through these IdeaData reviews and explore each of the applications in your list in detail. Such detailed research guarantee you weed out mismatched apps and choose the one that offers all the benefits your business requires for success.
Position of IdeaData in our main categories:
IdeaData is one of the top 100 Data Analytics Software products
Each business has its own characteristics, and may need a particular type of IT Development Software solution that will be adjusted to their company size, type of clients and employees and even specific niche they support. It's not wise to count on finding an ideal software that will be suitable for every business no matter what their background is. It may be a good idea to read a few IdeaData IT Development Software reviews first and even then you should remember what the software is intended to do for your company and your employees. Do you need an easy and straightforward solution with only essential features? Will you really use the complex functionalities needed by pros and large enterprises? Are there any specific features that are especially useful for the industry you work in? If you ask yourself these questions it will be much easier to locate a reliable app that will match your budget.
How Much Does IdeaData Cost?
IdeaData Pricing Plans:
Contact vendor
What are IdeaData pricing details?
IdeaData Pricing Plans:
Free Trial
Quote-based Plan
Contact vendor
CySight’s enterprise pricing information is available only by request.
User Satisfaction
We are aware that when you decide to purchase a IT Development Software it’s vital not only to see how professionals score it in their reviews, but also to check if the actual people and companies that bought this software are genuinely content with the service. That’s why we’ve created our behavior-based Customer Satisfaction Algorithm™ that gathers customer reviews, comments and IdeaData reviews across a wide range of social media sites. The information is then displayed in an easy to understand format showing how many customers had positive and negative experience with IdeaData. With that information at hand you will be ready to make an informed business choice that you won’t regret.
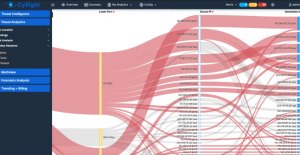
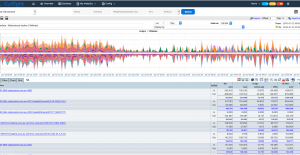
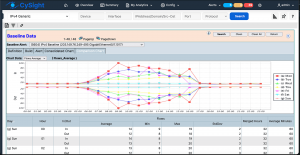
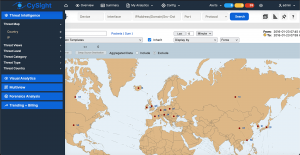
Screenshots
Technical details
Devices Supported
- Windows
- Linux
- Mac
- Web-based
Deployment
- Cloud Hosted
- On Premise
Language Support
- English
Pricing Model
- Quote-based
Customer Types
- Large Enterprises
- Medium Business
What Support Does This Vendor Offer?
- phone
- live support
- training
- tickets
What integrations are available for IdeaData?
CySight integrates with:
- Google Cloud
- Amazon Web Services (AWS)
- Azure
- VMware virtual machines
- Keysight Tech
- Gigamon
- Cisco
- Checkpoint
- Palo
- Mikrotik
- Ixia
- Switches
- Routers
- TAPs

IdeaData
is waiting for
your first review.

Write your own review of this product
ADD A REVIEWMore reviews from 0 actual users:






Join a community of 7,369 SaaS experts
Thank you for the time you take to leave a quick review of this software. Our community and review base is constantly developing because of experts like you, who are willing to share their experience and knowledge with others to help them make more informed buying decisions.
- Show the community that you're an actual user.
- We will only show your name and profile image in your review.
- You can still post your review anonymously.
OR
Sign in with company emailSign in with company email